For the Todo challenge, players where provided with an android apk named
todo.apk. This app was supposed to store todo lists and contained the flag.
Since apk files are just zip archives, I unzipped todo.apk and quickly found
the todos.db in the /assets/databases directory.
Running file todos.db revealed that it was a SQLite 3 database. So I could
query it after opening it with sqlite3 todos.db. The query .tables revealed
the todo table and the SELECT * FROM todo; presented two base64 encoded
entries.
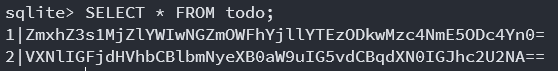
After decoding them, I found the flag.
flag{526eab04ff9aab9ea138903786a9878b}
Use actual encryption not just base64

